This article contains a writeup for the retired Hack The Box Marshal In The Middle challenge.
- Hack The Box Challenge page: https://app.hackthebox.com/challenges/27
- Time required: 30 min
The challenge has the following instructions:
The security team was alerted to suspicous network activity from a production web server.
Can you determine if any data was stolen and what it was?
Unpacking the archive
First, I check if I have the correct archive:
sha256sum "challenges/marshal_in_the_middle/Marshal in the Middle.zip"
I compare the checksum to the one given by Hack The Box, and it looks correct.
cdf53bab266ab4b8a28b943516bc064e9f966dae0a33503648694e15cb50ae2b challenges/marshal_in_the_middle/Marshal in the Middle.zip
I proceed by unpacking the archive:
unzip -P hackthebox \
"challenges/marshal_in_the_middle/Marshal in the Middle.zip" \
-d challenges/marshal_in_the_middle/ar/
This archive contains a packet capture file called chalcap.pcapng.
Archive: challenges/marshal_in_the_middle/Marshal in the Middle.zip
inflating: challenges/marshal_in_the_middle/ar/bro/conn.log
[...]
inflating: challenges/marshal_in_the_middle/ar/secrets.log
Deciphering the TLS conversations
I open chalcap.pcapng in Wireshark:
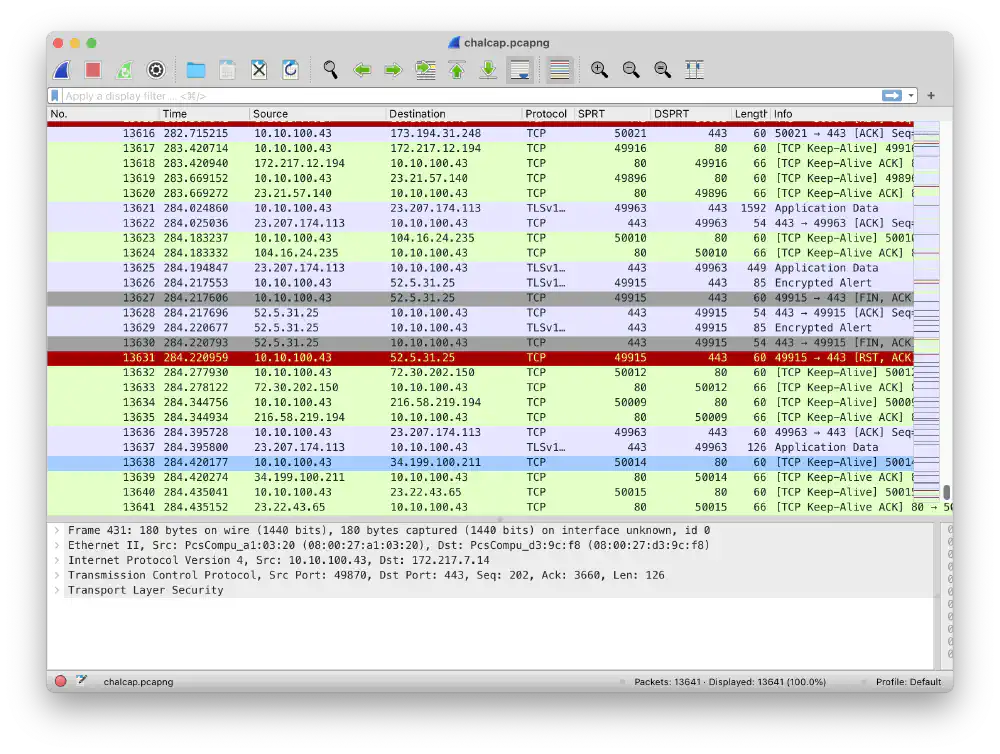
The packet dump chalcap.pcapng contains 13641 packets
Open in new tab
(full image size 297 KiB)
I try to decipher the individual TLS connections using bundle.pem. I also
need to tell Wireshark where it can find the key log secrets.log.
Learn more about how to decipher TLS traffic in Wireshark here.
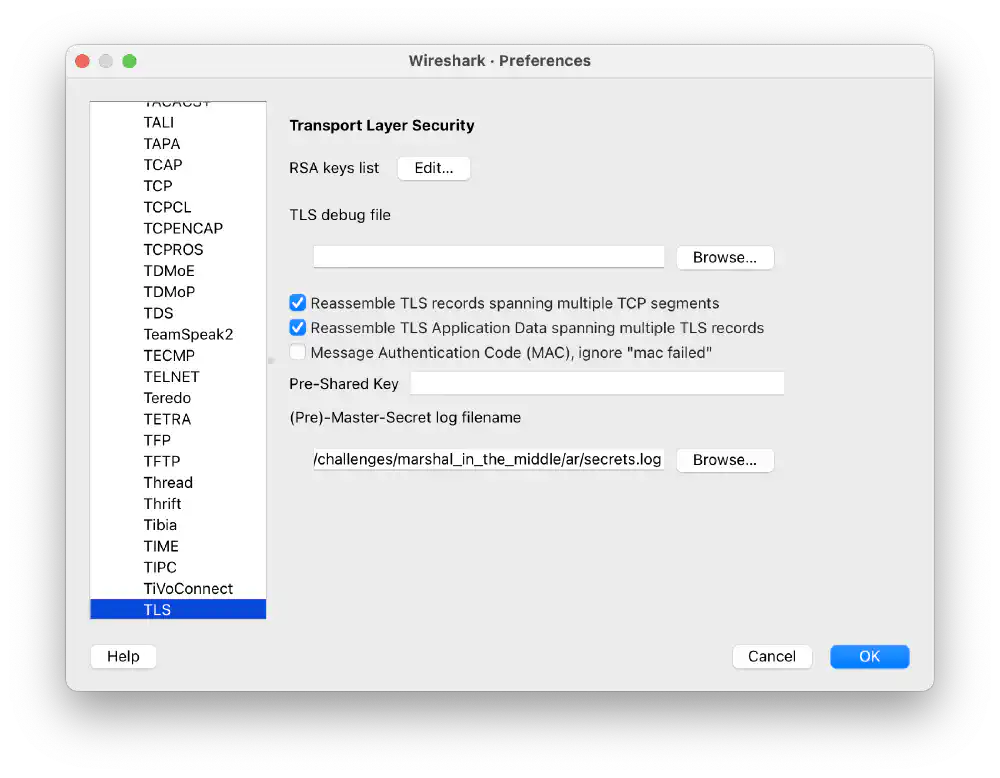
Screenshot of bundle.pem and secrets.log added to Wireshark
Open in new tab
(full image size 79 KiB)
Analyze individual conversations
I have deciphered all TLS conversations in the packet capture. I can now proceed in two different ways:
- Keep analyzing all connections by stripping away L1-L6 protocol headers. Work directly with L7 HTTP conversations
- Export all objects as retrieved through HTTP conversations
Stripping protocol headers
Use the “Export PDUs to File…” to strip away all L1-L6 information. Here, you can filter packets by HTTP, HTTP 2, and HTTP 3:
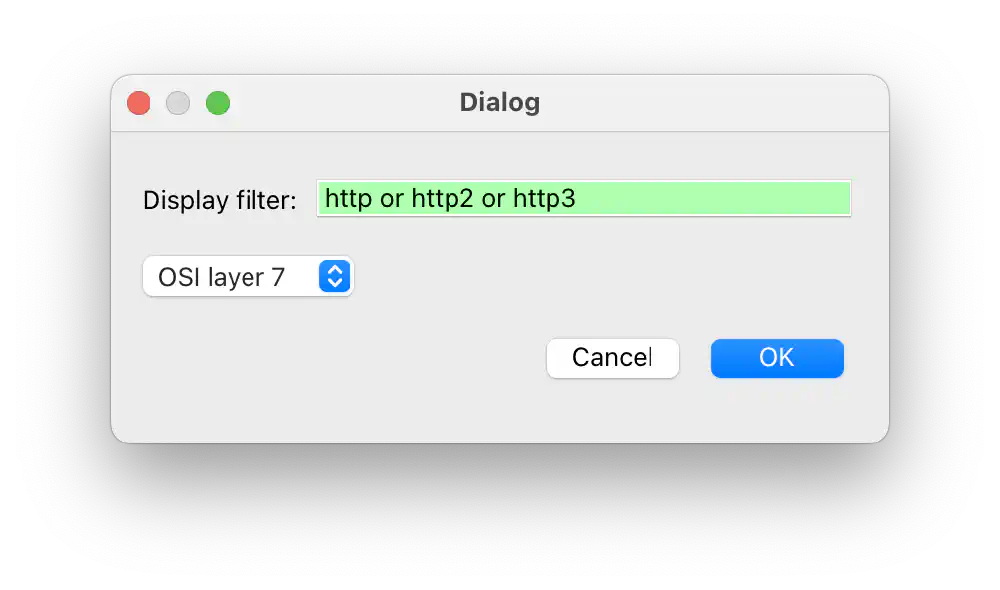
Exporting packet contents Open in new tab (full image size 39 KiB)
In a new Wireshark window, I see all HTTP conversations without their lower-layer protocol data:
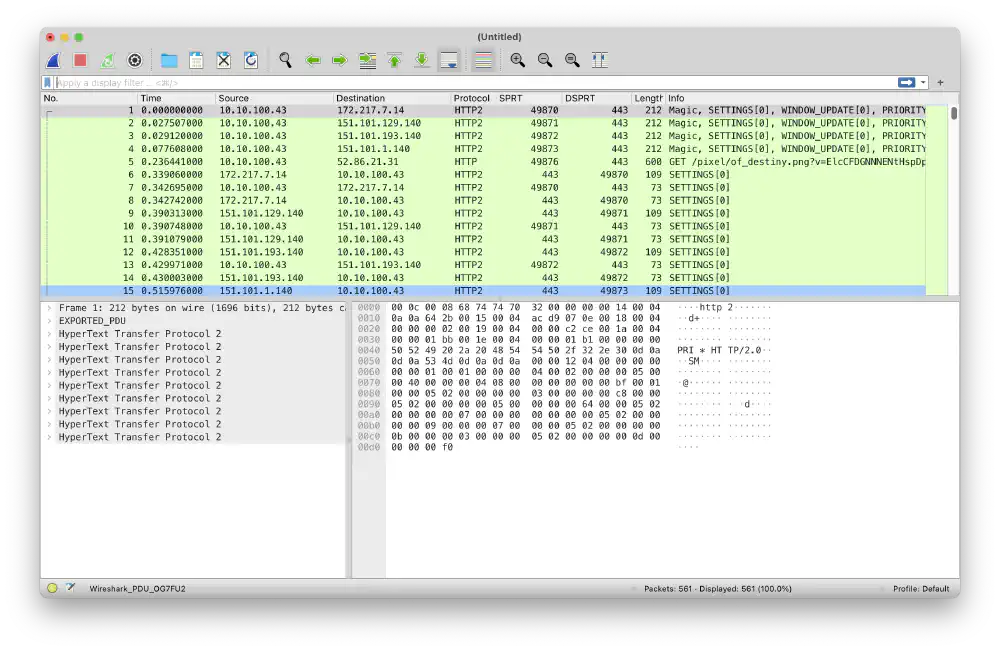
All L7 HTTP/2/3 conversations exported Open in new tab (full image size 258 KiB)
Here, you can filter by http.file_data contains "HTB" to show packets
containing the flag. Inspecting the packet contents manually then reveals the
flag.
Exporting HTTP objects
Wireshark can export all HTTP bodies directly with the “Export Objects” dialog:
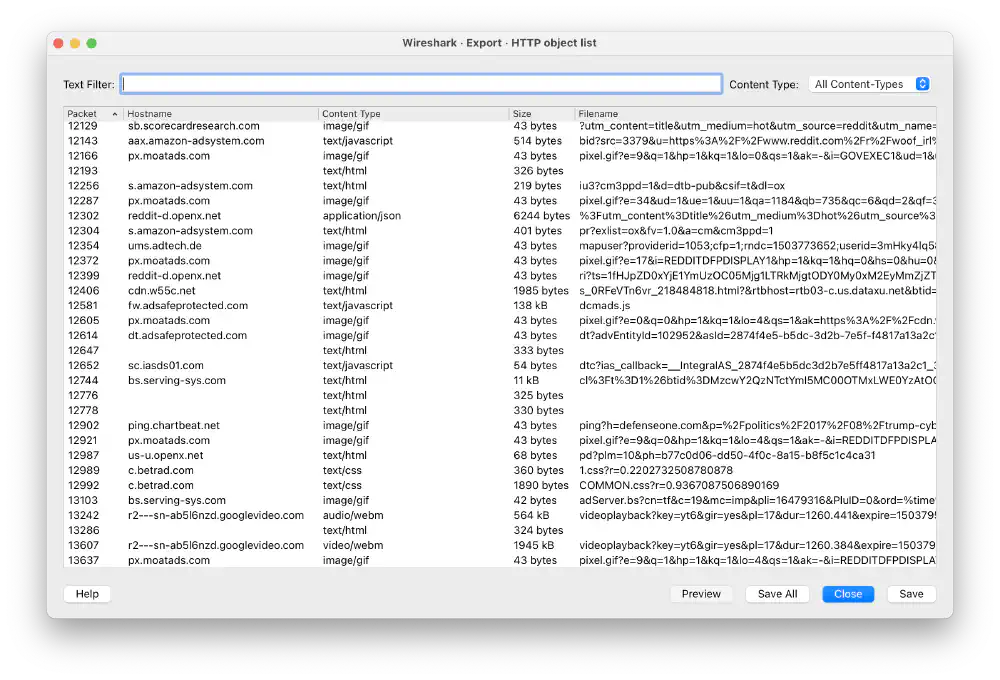
Exporting objects instead of PDUs Open in new tab (full image size 269 KiB)
I click “Save All” and store the HTTP objects in a new folder.
Grepping for the flag
Wireshark dumped all HTTP objects in a new folder. I can now search for the
flag by grepping for HTB:
grep -e "HTB" -r challenges/marshal_in_the_middle/http_objects/
grep immediately finds the flag:
challenges/marshal_in_the_middle/http_objects/api_post(4).php:HTB{...}
The file api_post(4).php contains a long array of American Express credit
card numbers. It appears that someone is stealing them. Better call the bank.
1 4m h4ckerm4n Open in new tab (full image size 63 KiB)
AAAAAAAAND, this again proves why forward secrecy is useful: it helps prevent exposure of confidential communications over HTTPS in case an attacker leaks key material. .